Financial Analytics
Financial analytics will analyze a company’s specific Financial data, processes, and functions. They will help investigate setting financial goals, forecasting,…
Computer-Generated Imagery
Computer-generated imagery is a computer graphics technology for developing and improving images in media, video games, and more. These are…
Data Mining
Data mining is searching and analyzing raw data to identify patterns and get helpful information. Many companies use data mining…
Data Access Arrangement
A data access arrangement is defined as the context of Telecommunications. That is specifically related to data communication and modems….
Edge AI
Edge AI or Edge Artificial Intelligence Is the process where AI computation is done closer to the user at the…
Haptic
Haptic technology will transmit and transfer information using sensations like touch or vibration. Nowadays, many artificial intelligence technologies use haptic…
Google Drive
Google Drive is a free service that Google provides that will allow you to store your data or files online…
Infographics
Infographics are crucial tools that are used for visual communication. Creating graphics uniquely and creatively to grab people’s attention is…
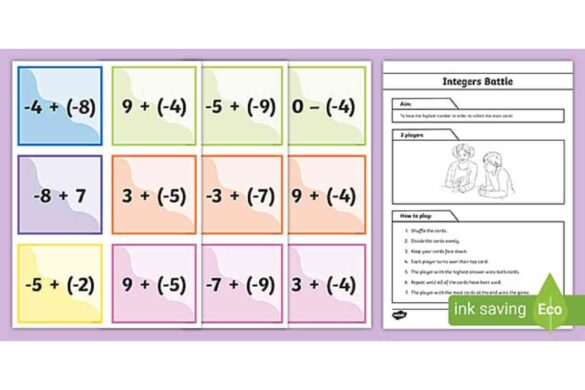
Integers
Integers are defined as whole numbers that will be positive, negative, or zero. They do not have any fractional or…
Hacking
Hacking is finding information and exploiting Someone’s computer system by gaining unauthorized access to their personal and organizational details. Well,…